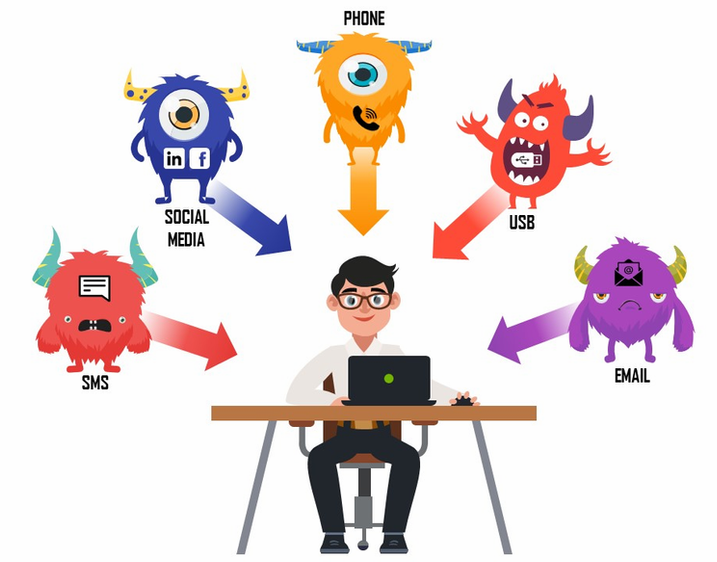
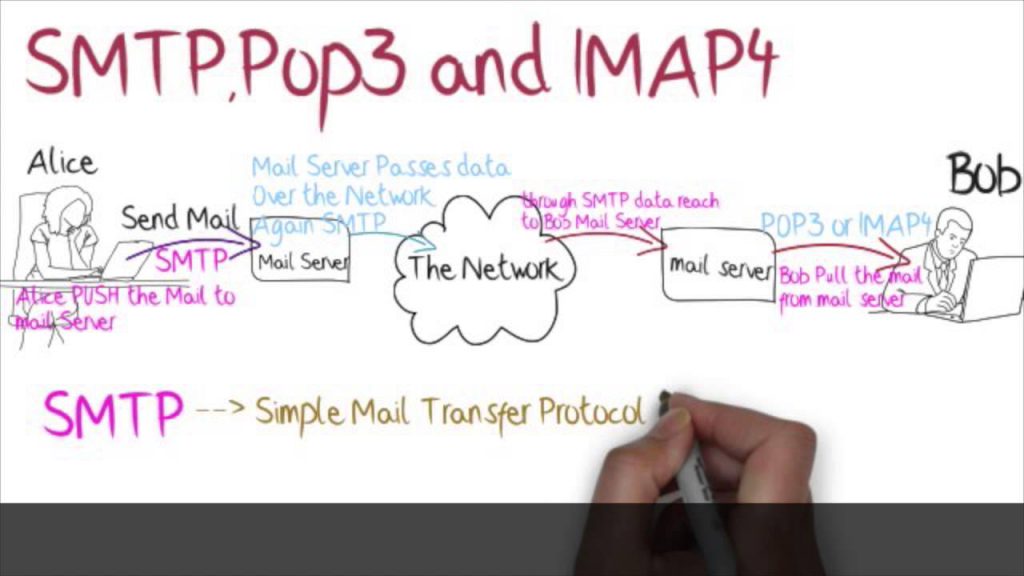
Phishing attacks & How to be safe from them.
The history of phishing reveals that the first phishing email originated sometime around the year 1995. Though, then the attacks were not so exceptional but still did the trick. Phishing attacks are often initiated through email communication. The phishing mail includes generic greetings as well as target’s name, phone number and other details to make […]
Phishing attacks & How to be safe from them. Read More »